
Standoff Cyberbones (free version)
An online simulator that offers a collection of real-life cases from the Standoff Cyberbattle
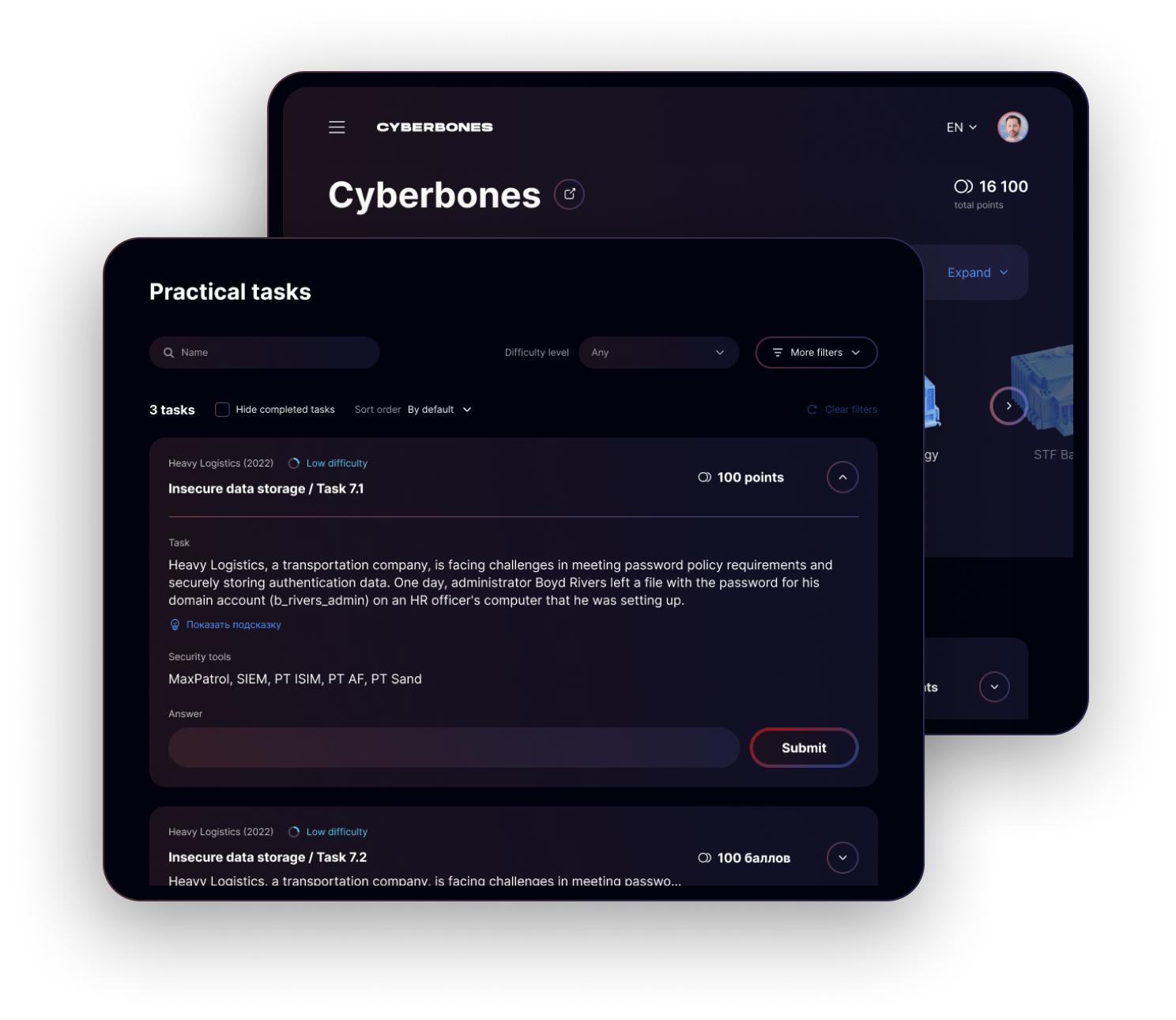
Infosec specialists sharpen skills in identifying and responding to cyberthreats
Examine strategies used by top red teams and learn how adversaries operate
Assistance with cybersecurity tools and incident investigations
To get started, just register on Standoff 365 and set up your VPN connection
Investigate cyberincidents at your own pace and convenience
Forge your cybersecurity team into hardened specialists by giving them hands-on practice using real cases
Accelerate onboarding for new hires and quickly assess entry-level skills
Test the latest versions of information security tools against real attacks
Investigate incidents with the same cutting-edge tools trusted by leading enterprises.

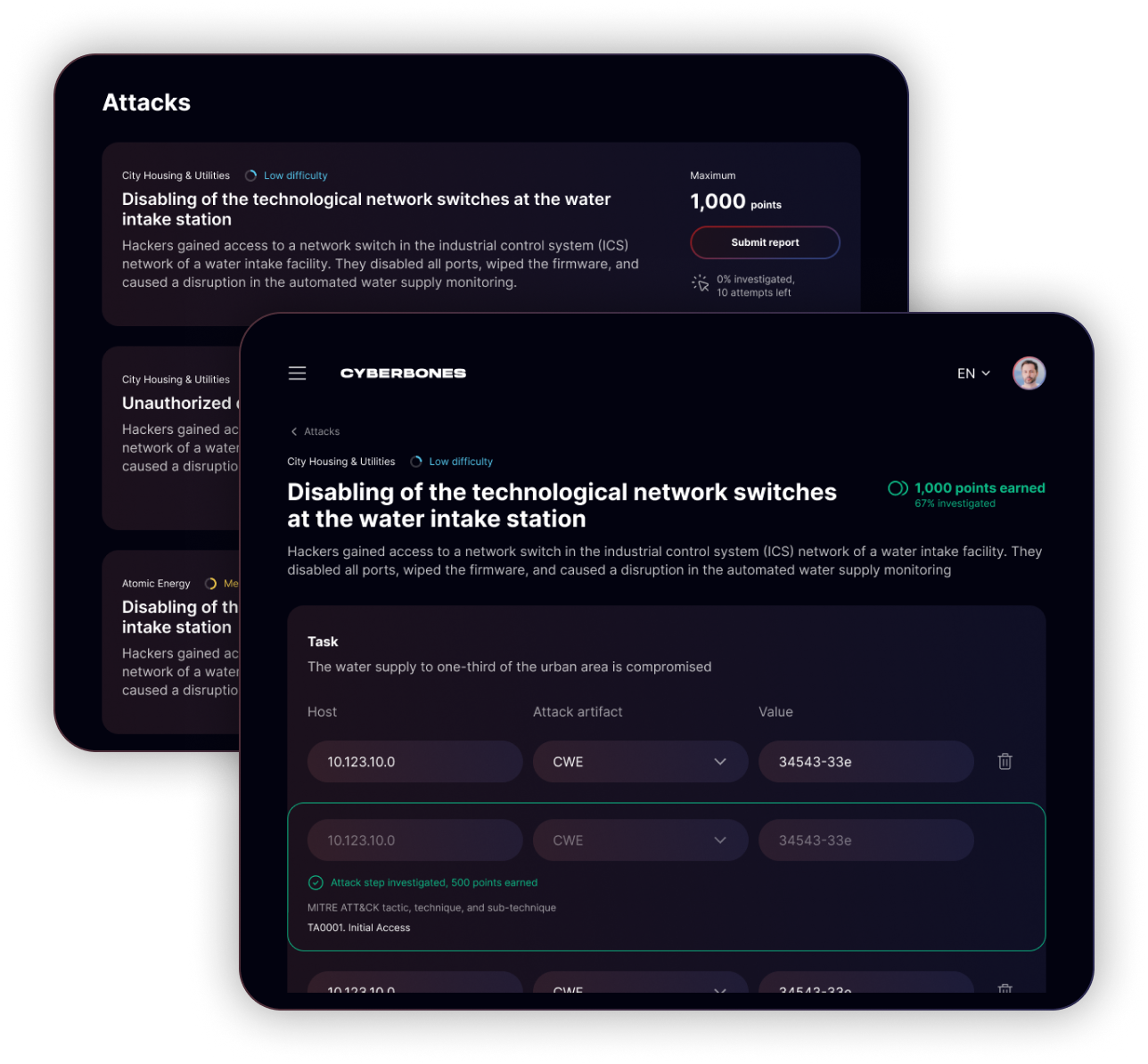
Standoff Cyberbones PRO version features 70+ diverse tasks based on Standoff Cyberbattle incidents, including complex attack chains.
Configurations are available for teams of 5, 10, or 15
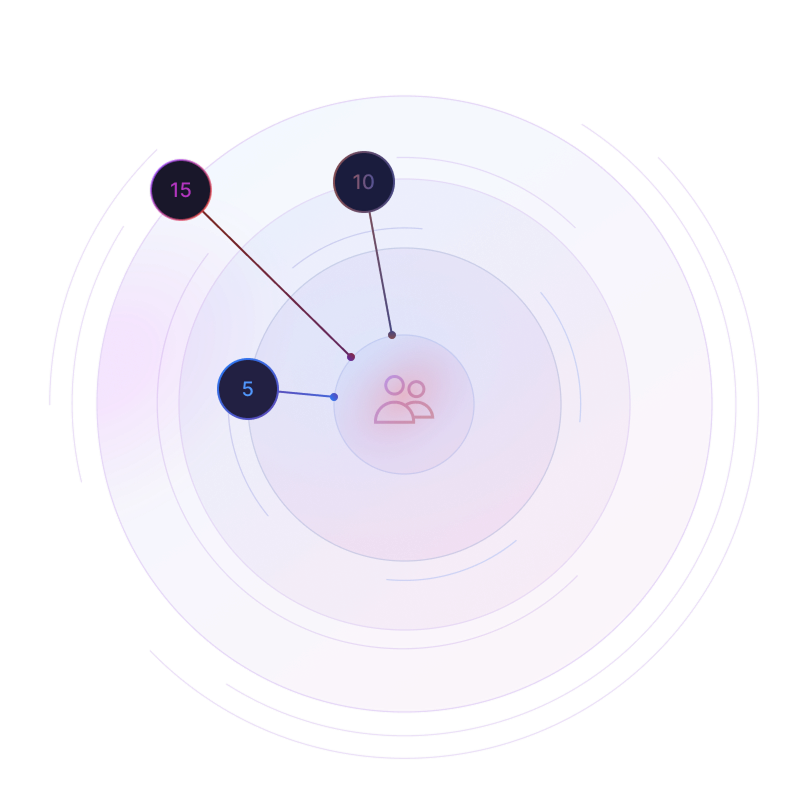
Select the option that best suits your goals
Ideal for intensive training, targeted preparation, or candidate skill assessment
Best for continuous team development, regular training integrated right into company workflows, and building robust skills

An online simulator that offers a collection of real-life cases from the Standoff Cyberbattle
Have questions about Standoff Cyberbones or Standoff 365? Drop us a note.
hello@standoff365.com
For businesses and cybersecurity professionals
| Standoff Cyberbones online simulator | Standoff Defend cyberrange | Standoff Cyberbattle | |
|---|---|---|---|
| Objective | ObjectiveSelf-guided practice in incident investigation using information security tools | ObjectiveComprehensive development of defensive security skills with mentor support | ObjectiveIntensive assessment of the team's readiness for real-time cyberattack response |
| Features | Features
| Features
| Features
|
| Task types | Task types Tasks based on Standoff Cyberbattle incidents | Task types
| Task types
|
| Attack format | Attack format Incidents from past Standoff cyberbattles | Attack format
| Attack format Live hacker attacks |
| Training format | Training formatSelf-guided | Training formatIndividual and team-based with mentor support | Training formatTeam-based with optional mentor support |
| Duration | Duration3 or 12 months | Duration12 months | Duration3–5 days |
| Mentor support | Mentor supportExpert support via Telegram bot | Mentor supportIndividual and team mentoring | Mentor supportOptional |
| Number of security tools | Number of security tools5 | Number of security tools5 | Number of security tools5 or more |
| Number of team members | Number of team membersFrom 5 to 15 | Number of team membersUp to 15 | Number of team membersUp to 15 |
| Service manager | Service manager— | Service manager | Service manager |
| Supplementary materials | Supplementary materials Quick start guides for security tools | Supplementary materials
| Supplementary materialsOptional |